In today’s interconnected digital landscape, managing network traffic efficiently and securely is paramount. Proxy servers play a crucial role in achieving this by acting as intermediaries between clients and servers. This comprehensive guide delves into the concept of proxy servers, their various types, applications, and the security considerations associated with their use.
What Is a Proxy Server?
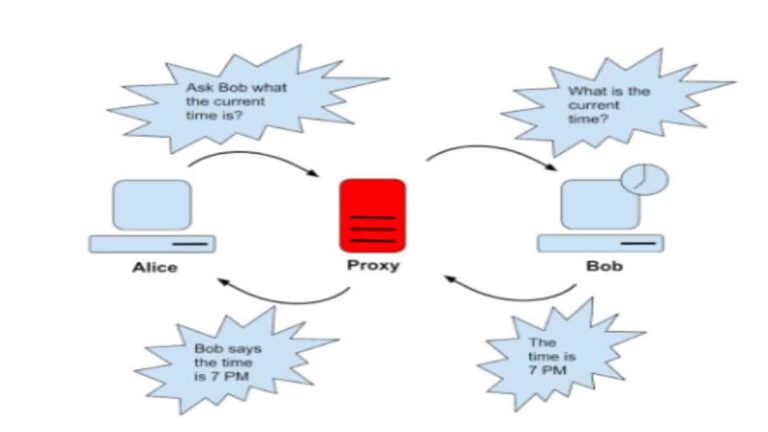
A proxy server is an intermediary system that sits between client devices and destination servers, forwarding client requests to the appropriate server and returning the server’s response to the client. This setup allows for enhanced security, improved performance, and administrative control over network traffic.
Types of Proxy Servers
Understanding the different types of proxy servers is essential for implementing the right solution for your network needs.
Forward Proxy
A forward proxy serves as an intermediary for client requests seeking resources from external servers. It is commonly used to retrieve data from a wide range of sources on the internet, providing functions such as content filtering, bandwidth control, and improved security by hiding client IP addresses.
Reverse Proxy
Positioned in front of web servers, a reverse proxy handles incoming requests from clients on behalf of the server. It offers benefits like load balancing, SSL encryption, caching of static content, and protection against malicious activities by masking the server’s IP address.
Transparent Proxy
Also known as an intercepting proxy, a transparent proxy intercepts client requests without requiring any special client configuration. While it simplifies administrative tasks and enforces acceptable use policies, it may introduce issues with HTTP authentication and caching.
Anonymous Proxy
An anonymous proxy server hides the client’s IP address from the destination server, providing a degree of anonymity during web browsing. However, the proxy server itself can still access the client’s information, necessitating trust in the proxy operator.
High-Anonymity Proxy
Also known as elite proxies, high-anonymity proxies conceal both the client’s IP address and the fact that a proxy is being used. This offers a higher level of anonymity, making it difficult for destination servers to detect proxy usage.
Distorting Proxy
A distorting proxy identifies itself as a proxy server but provides an incorrect client IP address to the destination server. This approach offers anonymity while allowing access to geo-restricted content by appearing as though the request originates from a permitted location.
Residential Proxy
Residential proxies route client requests through real devices with residential IP addresses assigned by Internet Service Providers (ISPs). This makes the traffic appear as if it originates from a regular household, aiding in activities like market research and accessing geo-blocked content.
Applications of Proxy Servers
Proxy servers are utilized in various scenarios to enhance network performance, security, and user experience.
Enhancing Security
By acting as intermediaries, proxy servers can prevent direct access to internal networks, reducing the risk of attacks. They can also filter malicious content and enforce security policies, safeguarding sensitive data.
Improving Performance
Caching proxies store copies of frequently accessed resources, reducing latency and bandwidth usage. This leads to faster response times and a more efficient network.
Bypassing Geo-Restrictions
Proxies can route traffic through servers in different locations, allowing users to access content restricted to specific regions. This is particularly useful for accessing region-specific services or content.
Monitoring and Filtering
Organizations use proxy servers to monitor employee internet usage, enforce acceptable use policies, and block access to inappropriate or non-work-related websites.
Load Balancing
Reverse proxies distribute client requests across multiple servers, ensuring no single server becomes overwhelmed. This load balancing improves reliability and scalability of services.
Security Considerations
While proxy servers offer numerous benefits, it’s essential to be aware of potential security implications.
Risks of Free Proxy Services
Utilizing free proxy services can pose significant risks. A study analyzing free web proxies revealed that many are unstable, vulnerable to security breaches, and may manipulate content, indicating potential malicious intent by proxy operators. Users are strongly cautioned against relying on free proxies due to these privacy and security concerns.
Data Privacy
Since proxy servers handle client requests and responses, they have access to potentially sensitive information. It’s crucial to ensure that proxy operators are trustworthy and that data is encrypted to prevent unauthorized access.
Legal and Ethical Implications
Using proxies to bypass geo-restrictions or access blocked content may violate terms of service or local laws. Organizations and individuals should consider the legal and ethical implications before implementing proxy solutions.
Conclusion
Proxy servers are vital tools in modern IT infrastructure, offering benefits like enhanced security, improved performance, and administrative control over network traffic. However, it’s essential to choose the appropriate type of proxy and be mindful of potential security and legal considerations. Implementing well-configured and trusted proxy servers can significantly contribute to a secure and efficient network environment.
Frequently Asked Questions (FAQs)
1. What is the primary function of a proxy server?
A proxy server acts as an intermediary between client devices and destination servers, forwarding client requests and returning server responses. This setup enhances security, performance, and administrative control over network traffic.
2. How does a forward proxy differ from a reverse proxy?
A forward proxy handles client requests seeking resources from external servers, often used for content filtering and anonymity. In contrast, a reverse proxy manages incoming requests on behalf of servers, providing load balancing, SSL encryption, and protection against malicious activities.
3. Are free proxy services safe to use?
Free proxy services often lack stability and may have security vulnerabilities. Studies have shown that many free proxies can manipulate content or expose users to malicious activities, posing significant privacy and security risks. It’s advisable to use trusted and secure proxy services.